A sophisticated malware campaign has emerged that leverages artificial intelligence to create deceptively legitimate applications, marking a significant evolution in cyberthreat tactics.
The EvilAI malware family represents a new breed of threats that combines AI-generated code with traditional trojan techniques to infiltrate systems worldwide while maintaining an unprecedented level of stealth.
The malware operates by disguising itself as productivity and AI-enhanced tools, complete with professional interfaces, valid digital signatures, and functional features that align with their advertised purposes.
Applications such as “Recipe Lister,” “Manual Finder,” and “PDF Editor” provide genuine utility to users while simultaneously executing malicious payloads in the background.
This dual-purpose approach significantly reduces user suspicion and allows the malware to establish persistence before detection.
Global telemetry data reveals the campaign’s extensive reach, with infections spanning multiple continents and affecting critical sectors including manufacturing, government services, and healthcare.
Europe has reported the highest concentration of cases with 56 incidents, followed by the Americas and AMEA regions with 29 cases each.
The rapid geographic distribution within just one week of monitoring indicates an active and expanding threat landscape.
Trend Micro researchers identified that EvilAI employs sophisticated social engineering tactics combined with AI-generated code that appears clean and legitimate to static analysis tools.
The threat actors create entirely novel applications rather than mimicking existing software brands, making detection considerably more challenging for traditional security solutions.
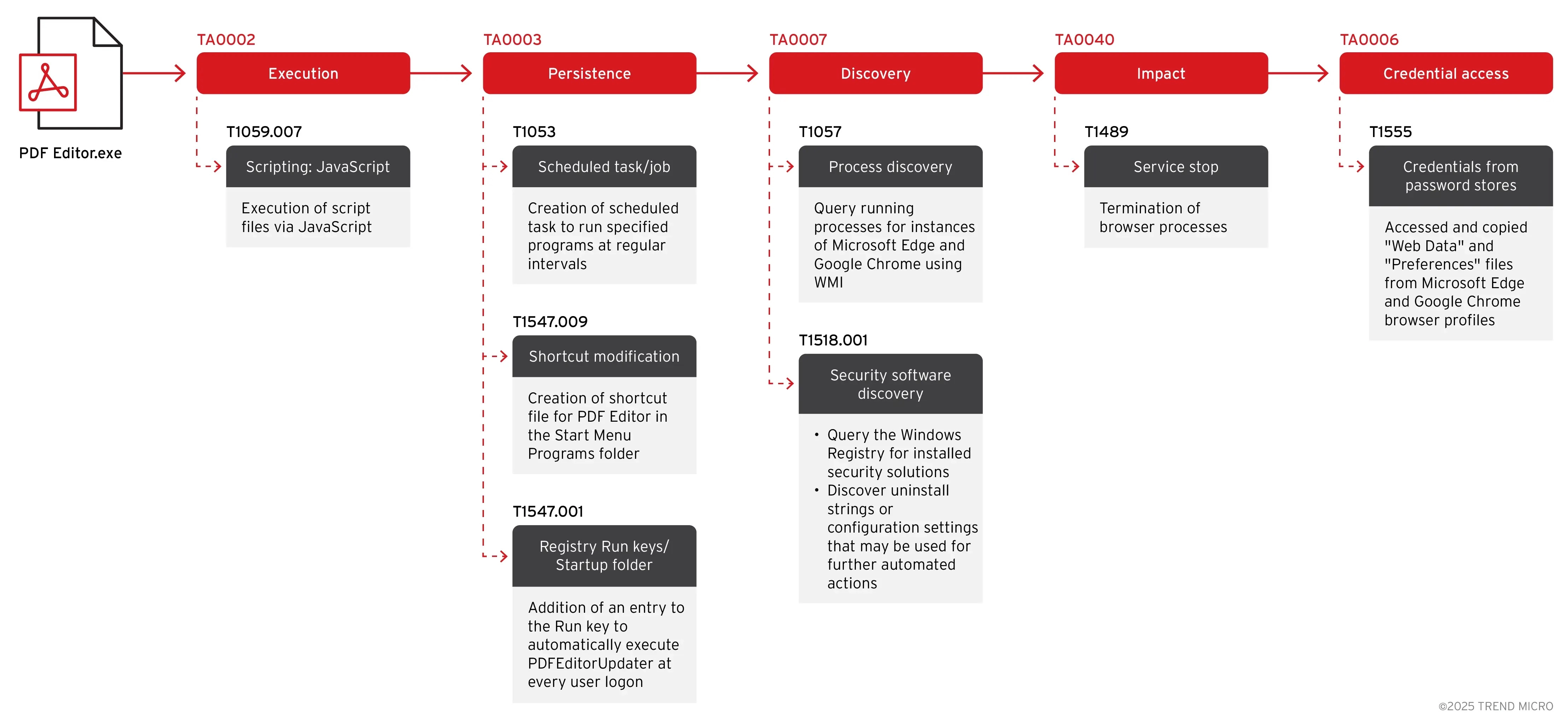
Advanced Infection and Persistence Mechanisms
The malware’s infection chain begins when users launch seemingly legitimate applications, triggering a covert Node.js execution process that remains hidden from user visibility.
The attack leverages a carefully orchestrated command sequence that silently launches node.exe via Windows command line, executing JavaScript payloads stored in temporary directories.
The persistence mechanism demonstrates remarkable sophistication through multiple redundant methods.
EvilAI creates scheduled tasks named “sys_component_health_{UID}” that masquerade as legitimate Windows processes, triggering daily at 10:51 AM and repeating every four hours. The implementation uses the following command structure:
schtasks /Create /TN "sys_component_health_{UID}" /TR "\"C:\Windows\system32\cmd[.]exe\" /c start \"\" /min \"%^LOCALAPPDATA^%\Programs\nodejs\node[.]exe\" \"%^LOCALAPPDATA^%\TEMP\{UID}or[.]js\"" /SC DAILY /ST 10:51 /RI 240 /DU 24:00 /FAdditionally, the malware establishes registry entries in the Windows Run key, ensuring execution at user logon while creating Start Menu shortcuts to maintain the illusion of legitimate software installation.
The JavaScript files consistently follow naming patterns with GUID suffixes ending in characters such as “or,” “ro,” or “of.”
EvilAI’s detection evasion capabilities extend beyond traditional obfuscation through the implementation of anti-analysis loops using MurmurHash3 32-bit hashing.
These loops create the appearance of potentially infinite execution cycles to static analysis tools while actually executing only once, effectively forcing analysts to rely on dynamic analysis methods rather than static code examination.



.webp)